





Createx Active Defense Infrastructure or CADI is a revolutionary solution designed and implemented by Createx System Works Ltd. for businesses who are open to new & emerging threats. Using enterprise solutions and products supported by our partner and alliance networks we are able to create a solutions for all markets (Small, Mid -Size, Large companies).

Call for more details.


Sophos Intercept X stops the widest range of attacks with a unique combination of deep learning malware detection, exploit prevention, anti-ransomware, and more.

Intelligent Endpoint Detection and Response (EDR)
The first EDR designed for security analysts and IT administrators
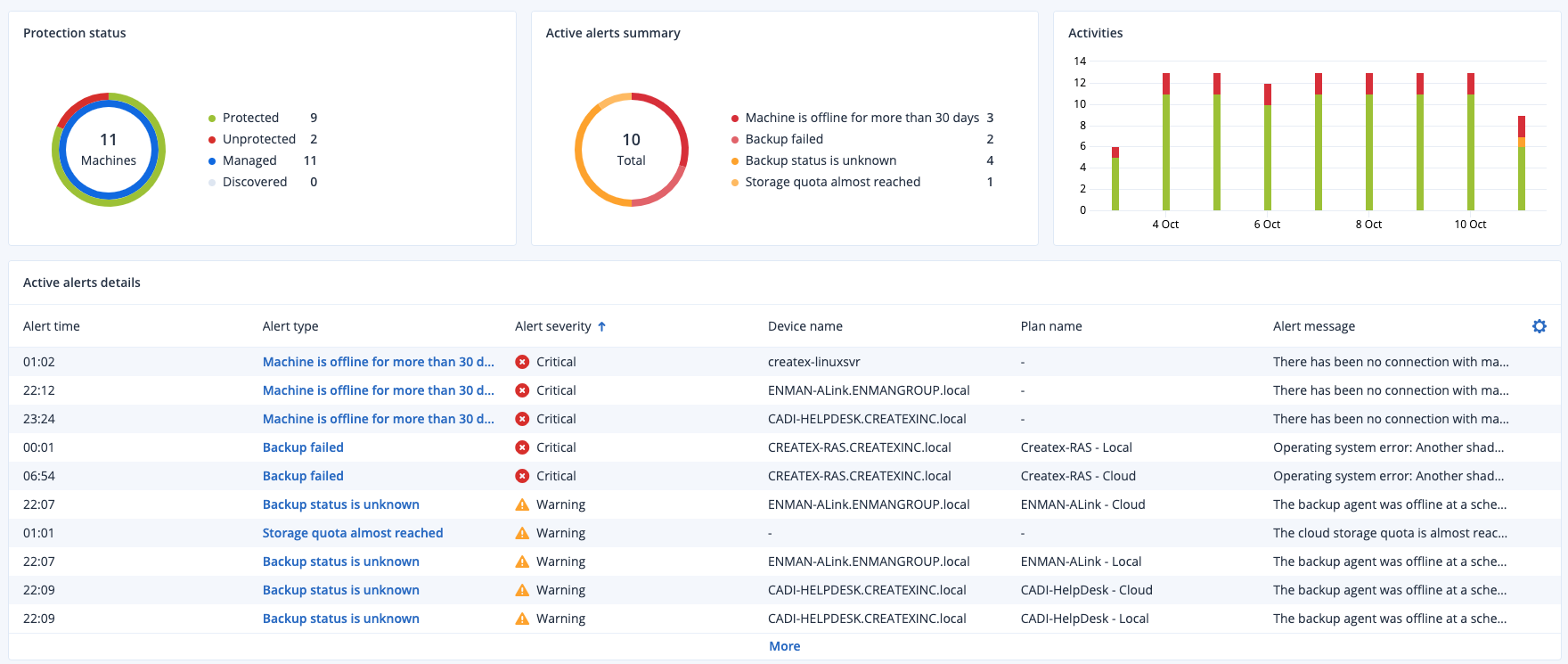
Intercept X Advanced with XDR allows you to ask any question about what has happened in the past, and what is happening now on your endpoints. Hunt threats to detect active adversaries, or leverage for IT operations to maintain IT security hygiene. When an issue is found remotely respond with precision. By starting with the strongest protection, Intercept X stops breaches before they start. It cuts down the number of items to investigate and saves you time.

Extended Detection and Response (XDR)
Intercept X Advanced with XDR goes beyond the endpoint, pulling in rich network, email, cloud and mobile* data sources to give you an even broader picture of your cybersecurity posture. You can quickly shift from a holistic view down into granular detail. For example:

Managed Threat Response (MTR)

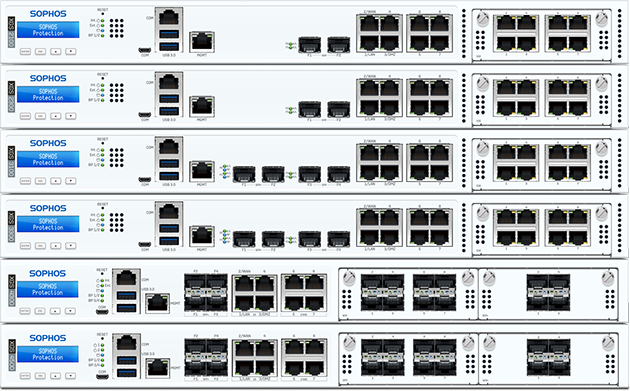
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These cyberattacks are usually aimed at accessing, changing, or destroying sensitive information; extorting money from users; or interrupting normal business processes.
Implementing effective cybersecurity measures is particularly challenging today because there are more devices than people, and attackers are becoming more innovative.
Our systems work with all company sizes from Home to Enterprise Solutions. Purchase or lease anyone of our solutions. Full Integration with our previous CADI System*.
Ask for a Demo
For more information and pricing contact us.
*Certain conditions may apply.

1-868-222-0930
sales@createxinc.com
1-868-741-4886
1-868-741-1128
1-868-221-3375
support@createxcss.com